Heard of TumbleBit but never really understood what it was? In part 1 of the series I explained what Tumblers are, their shortcomings, and why you need to watch the Breeze Wallet of Stratis to keep up with the developments of privacy within Bitcoin.
Making Bitcoin truly anonymous – Part 1
A little recap from part 1 tells us that the problem with traditional Tumblers comes down to two main problems. The first being anonymity, how can we make sure the Tumbler does not know who makes transactions to who? The second main problem is trustlessnes, how can we make sure we prevent a Tumbler from stealing? In this part 2 of the series about making Bitcoin truly anonymous, I will go further into details about how TumbleBit tackles deanonymization.

Anonymity
To explain how TumbleBit tackles deanonymization - thereby solving the privacy problem - I’ll use a simplified example to give a basic idea of the privacy process of TumbleBit. In this example I’ll illustrate a girl named Alice who wants to pay some guy named Yunk via Tumbler T (Tumbler of TumbleBit). Let’s say Alice wants to pay Yunk 1 bitcoin. She is afraid any normal Tumblers will deanonymize her or Yunk. This is how TumbleBit will solve the problem:
First of all, Tumbler T is a boss at puzzles. Since he is good at puzzles he created a bunch himself. Tumbler T pays 1 bitcoin for every solution to one of his puzzles. The Tumbler T is also willing to solve any puzzle for 1 bitcoin, not just the ones he created. To top it off, the Tumbler T even brags about being able to solve puzzles while being blindfolded, effectively not even seeing the puzzle he solves or the solution he will come up with. This game that Tumbler T set up with these set of rules will help Alice pay 1 bitcoin anonymously to Yunk. Here is how:
Alice chooses a puzzle of Tumbler T, says he should be blindfolded, and lets him solve the puzzle for 1 bitcoin. Tumbler T has no problem being blindfolded and solves the puzzle and gives the solution to Alice. Note that Tumbler T solves the puzzle but only knows a blindfolded version of the puzzle and the solution. Alice, in awe of the skills of Tumbler T, pays 1 bitcoin for his services. At this moment, Alice has paid Tumbler T 1 bitcoin for a solution to a puzzle, of which both Tumbler T only knows a ‘blinded’ version.
Afterwards, Alice gives Yunk the puzzle and the (unblinded) solution. Yunk let’s Tumbler T know he solved one of his puzzles and shows the puzzle and solution. Tumbler T looks at the solution, confirms it and gives Yunk the 1 bitcoin. Note that Tumbler T will never know that it is the solution he gave to Alice, since he did that blindfolded. Alice now payed Yunk 1 bitcoin without ever transferring bitcoins to him and without anyone being able to follow the trail back from Yunk to the fund’s original source Alice – resulting in deanonymization.
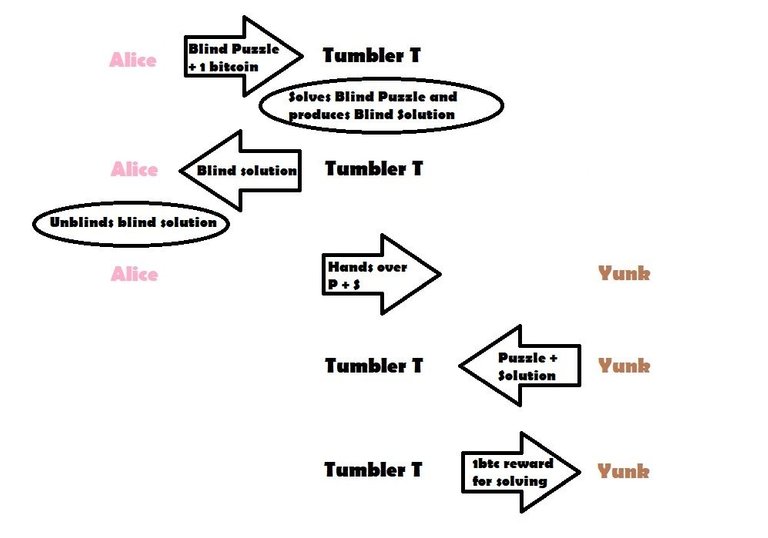
Although simplified, this illustration (respect the paint skills) shows the basic idea of TumbleBit’s anonymization process. There is however still the problem of trustlessness. How can we make sure we prevent Tumbler T from stealing? The final algorithm used for TumbleBit differs a lot since it is way more complex, mainly due to solving the issue of trust. To be able to fully explain the trustlessness of TumbleBit, I’ve decided to write part 3 of this series about the issue of trust and the way TumbleBit solves it. The comparison between TumbleBit and privacy-centric coins such as Monero and ZCash will be delayed to part 4.
For more info on TumbleBit go to:
For more info on the Breeze wallet go to:
Blog Stratisplatform StratisWiki
Stratis Slack
I am your follower, and i saw your posts. you are doing good:) @ronaldmcatee
Thanks, appreciate it! Part 3 is in the works, was enjoying my holiday a bit too much. Will post it in the coming days.
Welcome to steemit community. At Steemit we are all together like a Family. We help each other in information sharing and grow together along with steem community. Feel free to contact or follow me any time :) @hafizulislam
Nice work! Looking forward to Parts III and IV.