This Is Why The Allies Could Break The Enigma's Ciphers
In the beginning of this series we explored, what cryptography is and why it's useful. After that, we started getting into one of the most basic ways to encrypt something, which is a one time pad. Then we saw why people would much rather use a mechanical approach instead of one time pads. Now we're going to talk about the flaws in the enigma machine.
As with one time pads, and enigma machine that isn't properly implemented with display patterns in the cipher text (encrypted message). For a more detailed explanation of the patterns that might arise in a one time pad see my previous post.
The Flaws of The Engima
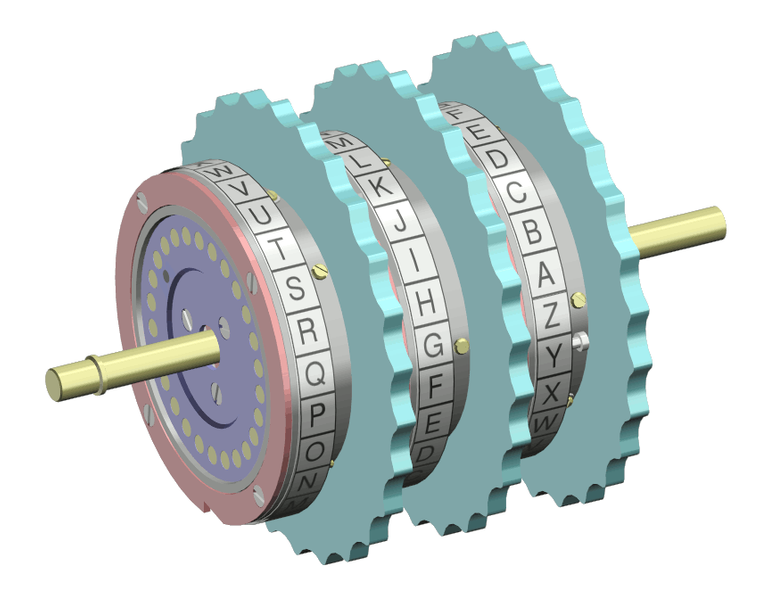
The first obvious flaw is the mapping between one rotor and the next. The 26 positions that each rotor could have don't each represent unrelated mappings, rather 26 offsets of one mapping. Ironically enough, the double step central rotor (which was intended to be an additional security measure) was actually another flaw in the design. It actually reduced the possible rotor combinations from 26 x 26 x 26 which would be 17,576 possible rotor combinations to 26 x 25 x 26 which would be 16,900
Single Stepping
possible rotor combinations
26 x 26 x 26 = 17,576
Double Stepping
possible rotor combinations:
26 x 25 x 26 = 16,900
These flaws alone would not have been enough to allow The Allied Forces to crack the code with their technology. However, their were also mistakes made in how The Axis Powers operated these machines that also made things easier (but not easy) for The Allied Forces.
Procedural Mistakes
1st Mistake: Same rotor settings
The same initial rotor settings were used all throughout one day. This was quickly corrected, but it gave The Allies enough information to work out what the rotor wiring was like. Thus, making the following attacks easier. They quickly corrected this mistake.
2nd Mistake: No repeated initial router settings in a month
At first glance you would think that this makes the encryptions more secure, but it actually decreases the entropy (randomness) by eliminating possibilities.
3rd Mistake: Redundancy
They would actually encrypt the key that was to decrypt the encoded message. They actually encrypted it twice using a known initial setting. Why would The Axis powers do that? Well, they did it to reduce mistakes. The problem is that it gave The Allies a pattern to look for, which allowed them to crack most of the daily messages. The Axis Powers soon corrected this mistake as well.
4th Mistake: Sending The Same Message With Different Encryptions
Another vulnerability was that when the same message was sent to two or more recipients some of whom didn't have enigma machines. If they don't have an enigma machine, they have to encrypt it some other way right. So naturally if two messages, that were encrypted differently, were intercepted and believed to be the same message they could be compared to identify patterns.
The Biggest Mistake
The setting of the plug board was only changed once per day. The plug board was a huge advancement in the enigma machine. A mere 10 cables could add 150,739,274,937,250(a whole lot of) possible combinations. Entropy measures the potential randomness of something in bits. This is calculated with log based 2 which would look something like this.
log2( 150,739,274,937,250) = 47.1 bits
So in other words, ten cables added 47.1 bits of entropy (randomness) to the encryptions.
A setting sheet for the patch cables was made and then distributed to all those intended to receive messages. There was one plugboard configuration for each day of the month.
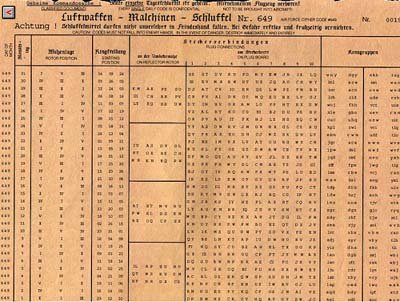
Since the configuration was only changed once per day, The Allies could combine the different messages they'd received that day. By combining information from all these messages, they could determine that day's configuration, and more easily decipher the messages. If The Axis Powers had changed the plugboard configurations more frequently, there would have been fewer messages to work with. The Axis Powers only needed The Allies to not figure out the message for about a week. The messages decay in relevance over time.
A day-old message is a military advantage.
A week-old message is a history lesson.
The plugboard made the enigma machine much better however there was a mistake made by its operator. As you will see time and again in cryptography, the weakest link is almost always the human operator.
How is this relevant to my Bitcoin?! Well, the moral of the story is be careful. You and the other humans that handle your keys and information and messages are always the weakest link. Strive for entropy and avoid patterns.
Congratulations @andrewholloway! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOP