Last night I finally took a bit of time to sit down and go through a few of my personal projects again. While clicking through them, there was one project that immediately stood out to me. I knew I had to try it out right away.

Some of you might already know that one of my hobbies is security research. I spend a lot of my free time digging into applications, trying to understand how they work, and sometimes even finding security issues. Yesterday I was testing out a new tool that helps scan for vulnerabilities, and I decided to run it on a group of GitHub repositories that are connected to the Hive blockchain.
I set everything up by installing the script and adding all ten repositories into a clean folder structure so I could go through them one by one.
By the time I reached the third project, I already found something that really made me pause. It was the kind of discovery that makes you think twice. Of course, I am not going to mention the name of the project or the person behind it, because I have already sent them a private message and I am still waiting for a reply.
But I do want to say something to everyone who maintains public code on GitHub or similar platforms. Please be careful and avoid uploading any private API keys directly into your files. I know it might seem easier at first, but it is really risky and there are better and safer ways to handle it.
Just to give you an idea of what I found, here is a small part of the file I came across. I have blurred or hidden the sensitive details, of course, to protect the project and the owner.
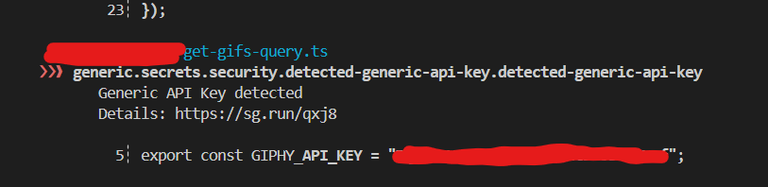
If you are running an open-source project, or even just working on something small for fun, it is always worth double-checking what you are pushing online. Mistakes happen, but when it comes to security, a small slip can cause big problems later on.
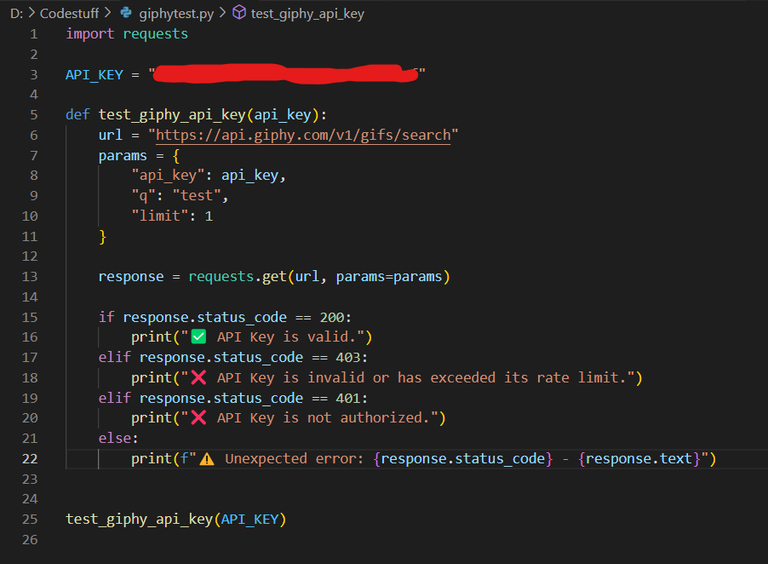
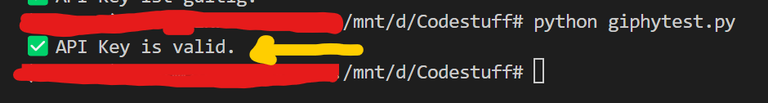
And yes, by the way, the key I found is valid. I was able to confirm that very quickly and easily using a small Python script. It only took a few lines of code to check whether the key was real.
Back on Steem I found a few active keys, one as much as 80K Steem on the account. Fortunately, was able to get in touch with them before anyone took it.
Wow, that is pretty scary! I'm glad you handled it ethically and you reached out to the person who owns the keys. I don't think my stuff is that in depth, but it definitely has me thinking I need to check out my github to make sure I haven't done something similar.
Congratulations @louis88! You received a personal badge!
Wait until the end of Power Up Day to find out the size of your Power-Bee.
May the Hive Power be with you!
You can view your badges on your board and compare yourself to others in the Ranking
Check out our last posts: