
IMG: Pixabay
Hello there, Leaners! On this first occasion, I will complete a Stage-o2 task: I will discuss the security keys on the hive.blog platform and will answer all these questions:
How much do you know about the security keys of Hive?
Do you have enough idea about the importance of these keys?
Do you know how to locate security keys of Hive?
What are the functions/permissions of each keys and explain them?
What measures have you taken to keep your keys safe?
But, before I get into that, let me first explain cryptocurrency so that you can see how it relates to some security on hive.blog later.
As we all know, cryptocurrencies have grown in popularity in recent years. Many cryptocurrency enthusiasts even prefer to save in digital currency rather than fiat currency.
What exactly does the term "cryptocurrency" mean?
Cryptocurrency is a linguistic combination of two words: cryptography (secret code) and currency (money). In layman's terms, cryptocurrency refers to the digital currency that is created and safeguarded using secret codes.
There are numerous types of cryptocurrency that are currently in use around the world. From the cheapest to the most expensive. This first crypto currency, like bitcoin, has a million-dollar price tag.
Cryptocurrencies cannot be manipulated because they are created and protected by secret codes. It is not possible to create fake digital currency from real currency. You cannot create your own bitcoins. And all digital currencies circulating around the world will be recorded neatly in a financial administration book called blockchain. All trips or transactions of digital currency coins are recorded in the book.
Digital currency (cryptocurrency) operates in a decentralized manner, which means that the currency is not held in authority by anyone other than the currency and its owner. When you own multiple digital currency coins, you have complete control over the money.
Because it necessitates a completely secure wallet in order for the coins you possess to be completely safe. If you have traditional money in the form of paper and keep it in your wallet, you may keep it in the safest place where you believe no one will notice.
Because digital currency cannot be physically touched, the wallet that you require is also a virtual wallet. And, to keep your wallet secure, you'll need a key or security code that only you know.
The brief explanation above should help you understand the significance of security keys and how they should be applied to your digital assets. One of them is the hive security key, which we will discuss later.

IMG: #stockimages by. @my451r
Looking at the hive platform or reading the whitepaper, it is clear that the Hive network includes two cryptocurrency asset classes: HIVE and Hive Backed Dollars (HBD).
Furthermore, HIVE is available in both a liquid (simply called HIVE) and a staked form (called Hive Power). Hive Power (HP), a type of HIVE at stake, is distributed during a process known as a "power-up." Once activated, the Hive Power can be completely or partially unstashed at any time, a process known as "Power Down."
The staked HIVE is then converted to liquid form (ie HIVE) in equal amounts over a 13-week period, with segments delivered every 7 days.
There is a wallet on the hive.blog platform where you can store your assets, whether they are in the form of liquid hives, power hives, or HBD hives. Secret keys are required to maintain the security of your account and ensure the protection of these assets.
What are the keys contained in the hive platform? I'll go over them one by one now.
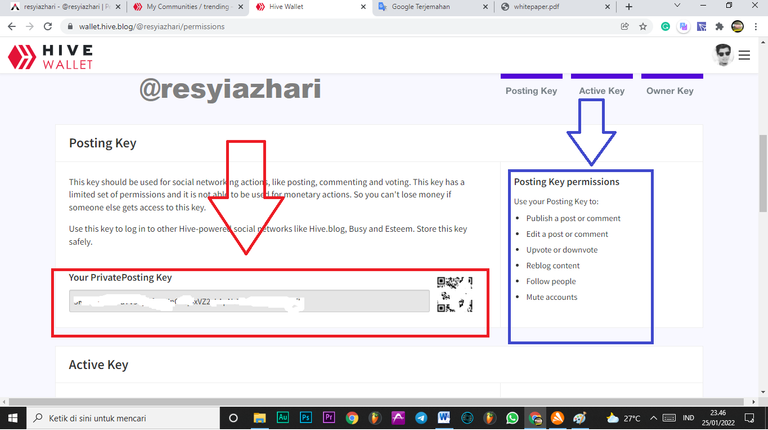
Posting Key
This key is used for social gatherings (posting, commenting and voting). This key has restricted permissions and cannot be used for monetary transactions. As a result, if someone else obtains access to this key, you will not suffer financial loss.
Post keys and other keys from your wallet are available. By:
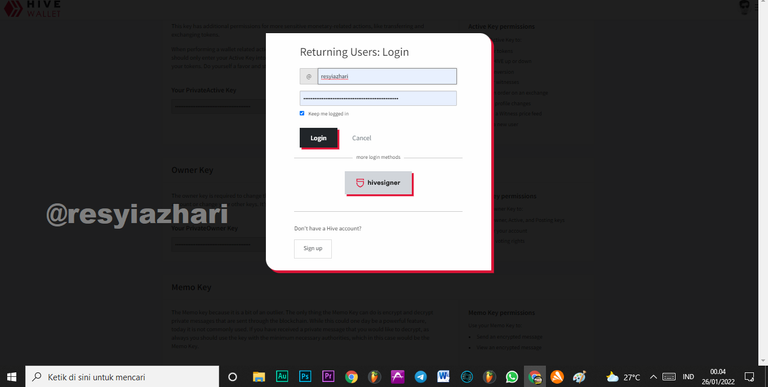
1. Tap your profile picture, then select Wallet
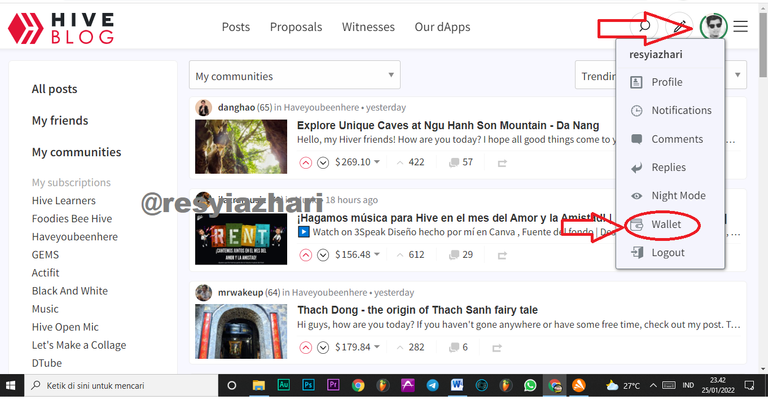
2. There are several options inside the swallow. Please select the Key & Permission tab.
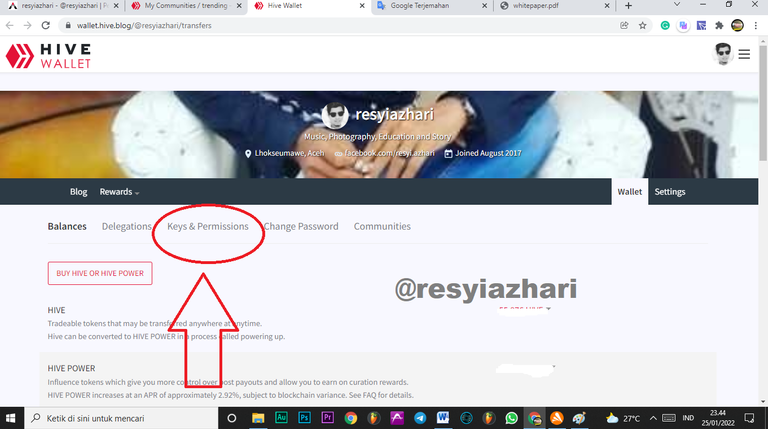
3. You will immediately see your post key there (Red Box)
4. The purpose of the post key can be found on the right side of the key (Blue box).
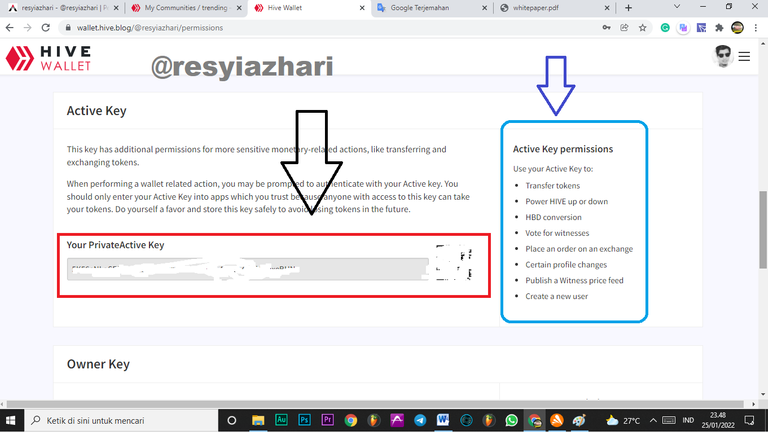
Active Key
The active key is situated directly beneath the posting key. This key has additional permissions for more sensitive monetary transactions, such as token transfer and exchange.
This key, unlike a posting key, cannot be seen right away because it has sensitive monetary permissions. To obtain the key, you must first press reveal and then login again. If you can't see the active key, you'll need to use your primary key.
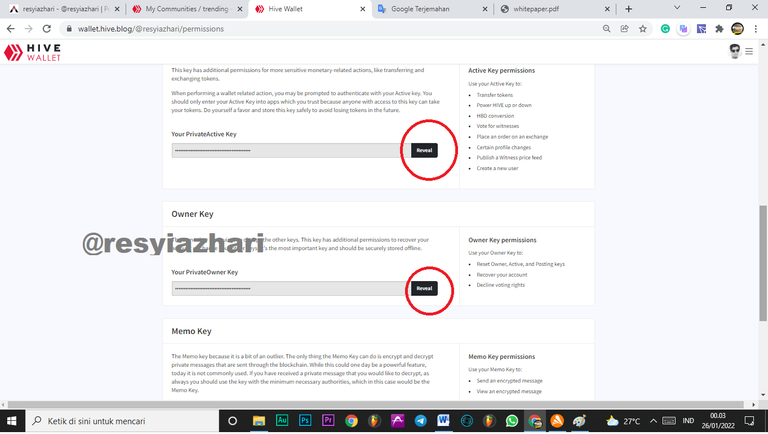
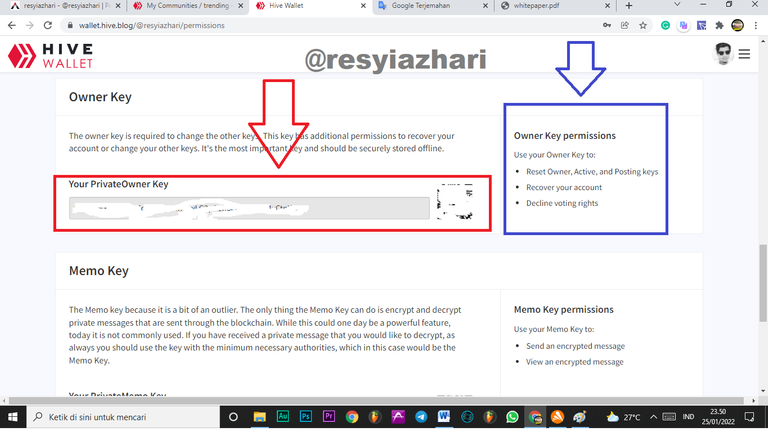
Owner Key
This owner key, like the active key, has a more sensitive function than the active key. This key, which is the Owner key, is required to change the other keys. This key has the ability to restore your account or change other keys.
So, in order to see it, you must also do as well the way to see the active key.


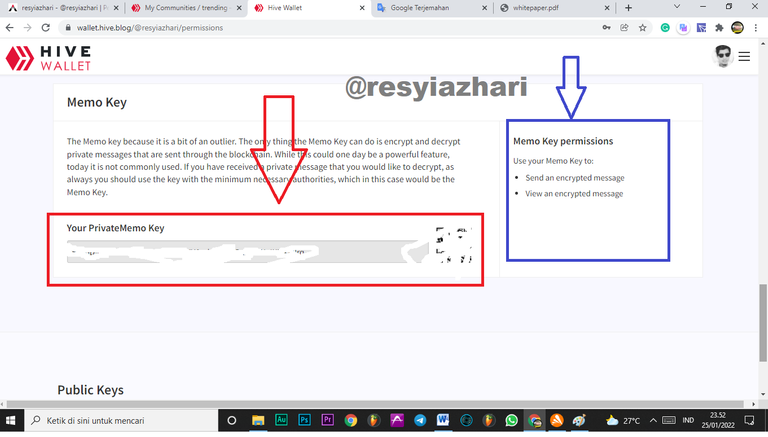
Memo key.
Memo Key's only capability is to encrypt and decrypt private messages sent over the blockchain.
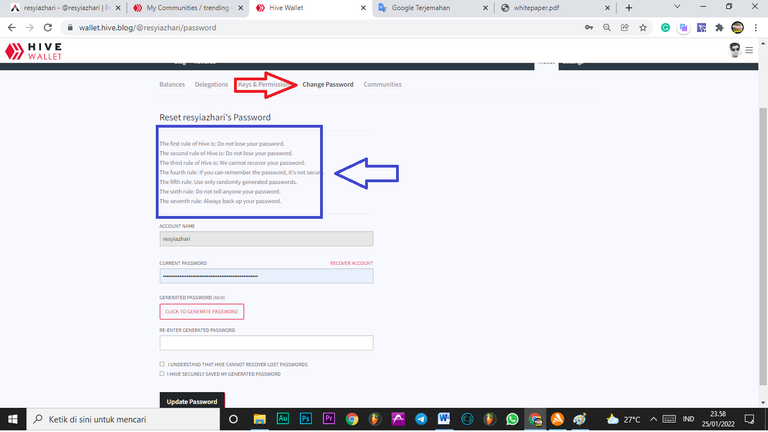
In addition to the key and permission options, the wallet also includes the ability to change your master password and account lock. However, before making changes to the primary key, you must first read the terms. That is to say:
The first rule of Hive is to never forget your password.
The second rule of Hive is to never forget your password.
The third rule of Hive is that we cannot recover your password.
The fourth rule is that if you can remember the password, it is not secure.
Fifth, only use passwords that are generated at random.
Sixth rule: Never reveal your password to anyone.
The seventh rule is to always backup your passwords.
I've made certain that my key storage area is completely secure. because of a few things I've done:
- I made a record on paper, kept it, and my wife and I were aware of it.
- I forwarded it to a few of my e-mail addresses. There is no need for you to be concerned about the email's security. Because I previously tampered with the password I sent via emails, such as by replacing uppercase and lowercase letters, and others which I will not mention here


FOLLOW ME ON
DISCORD FACEBOOK INSTAGRAM TELEGRAM TWITTER

The rewards earned on this comment will go directly to the person sharing the post on Twitter as long as they are registered with @poshtoken. Sign up at https://hiveposh.com.
Wow! This is brilliant @resyiazhari it’s so educative and probably the best I’ve read so far.
Thank you for this.
Thank you for the compliment.