The thing that bothers me the most about this, is how awful that lie is. What the fuck is a "Hive Email Database" even supposed to be? Even if there was one, why would that put an account's keys at risk? How many people signed up with an email anyways? Of those people, why would they think their key is attached to it?
Unfortunately, I know some people may still fall for this, but god damn I hate when scams seem to not even try. For instance, their whole scam is just a ploy to get you to enter your private key into a fake HiveSigner page:
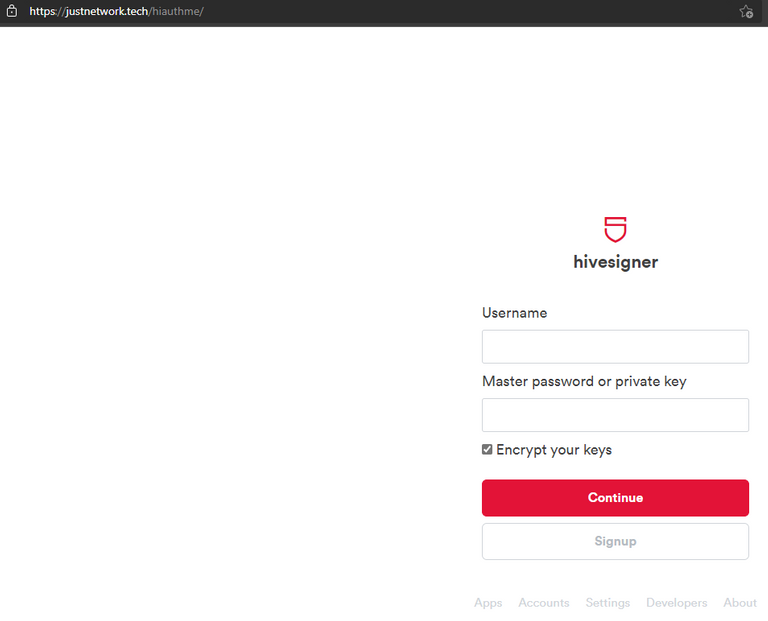
Look legit, right? (well, expect for that domain, which by the way hosts a fake steemconnect app on it's main page) Here's where their lack of efforts reveal themselves. Click on any of those links in the footer (Apps, Accounts, etc.), and you'll see the scammers didn't even bother implementing something for them:
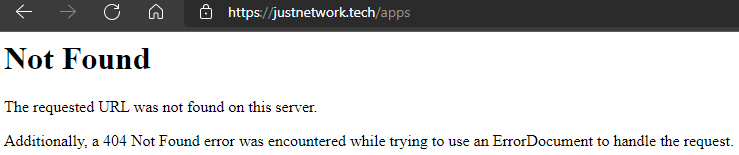
It's truly bottom of the barrel effort here, and even then it's still so pathetic.
By the way, when you enter a key into that fake HiveSigner app, for those curious, it submits your username & key to the scammers database, so they can harvest them & presumably lock you out of your account before draining all of the funds, and then responds with:
{"msg":"success","url":"https:\/\/justnetwork.tech\/hiauthme\/thank-you.php"}
Which basically just ends up redirecting your browser to show this:

No actual account -> key verification checking... So... I'm not saying you should flood their fake HiveSigner app with a bunch of fake username + key combinations... I'm just saying if one were to write a script that just submits fake data every second & runs in non-stop... Technically, it would be very hard for the scammers to wade through the bullshit data to find the real data. Unless they wrote a script themselves to auto try all the data they get... Which would mean we'd want several good guys to run the fake-data script all day every day... Anyways, I'm just pointing out the obvious here, and totally not suggesting anything...
Thanks for you work in fighting this.
I do run it every time and noticed that when I do their next attack starts later because they spent more time trying the thousands of credentials (script, multiple people manually? Not sure).
In other attacks they were trying to collect people’s username and passwords to do credentials stuffing into their email provider. I suspect that’s how they found a private key of a user that unfortunately lost 200 k 😌
Right, I forgot about the sign up emails. I created my accounts through code and paying 3 HIVE :)
1 - https://hive.blog/@keys-defender/watch-out-new-phishing-wave-do-not-vote-for-leofinance-using-that-link-its-phishing
2 - https://hive.blog/@keys-defender/new-phishing-wave-do-not-fall-for-it-there-is-no-mainnet-launch
3 - https://hive.blog/@keys-defender/there-is-no-airdrop-it-s-just-phishing
4 - https://hive.blog/@keys-defender/phishing-campaign-on-hive-be-aware
I’ll tell you more (since this is not sensitive anymore). A few months back their profile ID leaked into their phishing page code so I was able to programmatically poll that profile every 30s to found out immediately when they published a new phishing site. That way multiple times their attack stopped immediacy because they were already discovered. I must have driven them crazy because eventually they stopped (or at least for a couple of months - until now that they started using a different hosting provider).
There is also great work by other people like @guiltyparties and @louis88 that immediately contact the hosting services to take the phishing site down!
We are collecting more intel on them as they keep making mistakes. Stay tuned 😉
Ah, I see you're way ahead of me on that one 😅
Yeah, I noticed this recent domain is being hosted on
web.appwhich I believe is a Google hosting service, so hopefully it'll be easy to send in phishing reports.Again, great work fighting against these attacks. Cheers! 🍻
Thanks, and thank you for the delegation as well! =]