
There are a handful of stories about people being harassed or kidnapped for their crypto holdings. Now, before you brush these off as attacks targeting high-profile individuals, retail investors are also at risk; all it takes is for your real-world identity to be linked to your crypto wallet.
You may have missed this story. But in May 2025, 37-year-old John Woeltz was arrested for allegedly kidnapping and torturing an Italian man for his crypto holdings. Woeltz, who has been lauded as the “crypto king of Kentucky,” held his captive for nearly three weeks in his luxury NoLIta apartment.
The victim, Michael Valentino Teofrasto Carturan, was a business partner of Woeltz. Carturan’s rumoured crypto wealth, reportedly worth millions, was the perfect trigger for a brutal attack that included assault, being held at gunpoint, and being suspended from the top floor of the building.
I know you’ve been sold the popular narrative that blockchains are an impenetrable fortress of security and privacy. But what happens when data leaks on the blockchain? Do you even know what public ledgers really reveal?
A simple Bitcoin Transaction
There is a clear difference between anonymity and pseudonymity. Most public blockchains, like Bitcoin and Ethereum, are fundamentally pseudonymous, not anonymous.
Anonymity means that a user’s identity is completely unknown, and their actions cannot be traced back to them. Take a cash transaction, for example, it is difficult to link the money to the person who spent it. Pseudonymity, on the other hand, means that a user’s real-world identity is hidden behind a public address (a “pseudonym”). All transactions are linked to this address, creating a transparent, public history of activity.
This is where the illusion of privacy begins to crumble. While your name and physical address aren’t explicitly on the blockchain, your public key and the associated transactions are. Each time you interact with the network, you create a permanent, unchangeable record.
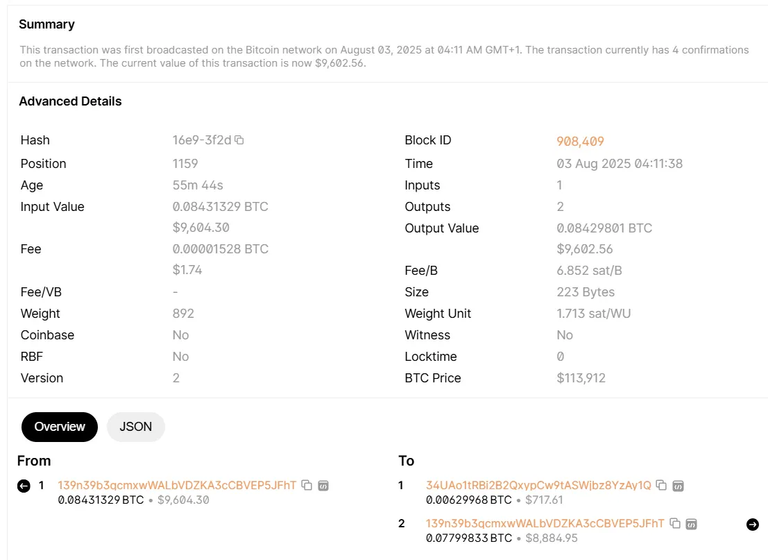
For the sake of illustration, I pulled a random transaction from the Bitcoin explorer. As seen in the image above, the transaction was broadcast on the Bitcoin network on August 03, 2025. Other details we can pull from this image include:
- The Transaction ID (TxID): A unique, 32-byte code that serves as the transaction’s permanent identifier.
- Sending and Receiving Addresses: Two pseudonymous addresses that show the direction of the funds — one for the sender and one for the receiver.
- Timestamp: A record of when the transaction’s block was officially added to the blockchain.
- The Amounts: The specific value of Bitcoin that changed hands.
I’ll be completely honest — this data is useless to me and millions of others like myself because it begs for more context. For instance, who are the entities behind the transaction (an exchange, a p2p transaction, or a malicious actor) and what is the purpose of the transaction?
While I may not be able to decode transparent blockchain data, this public trail is a goldmine for data analytics firms and malicious actors who employ sophisticated techniques to connect these pseudonyms to real-world identities. It’s no longer news that all Bitcoin transactions are public and traceable. This is the same for many other blockchains.
How Public Data Becomes Personal
Here are some of the ways this public data is used to “de-anonymize” users:
- Transaction Linking and Cluster Analysis: Blockchain analytics companies can monitor and analyse transaction patterns. By identifying a user’s wallet address and linking it to other addresses they’ve interacted with, a pattern emerges. If a single address receives funds from multiple sources and then sends those funds to a known exchange that requires KYC (Know Your Customer) information, the user’s identity can be tied to that address. This process, known as “cluster analysis,” can create a comprehensive profile of a user’s on-chain activity.
- Public IP Addresses and Network Attacks: Even with a public ledger, a user’s interaction with the blockchain requires an internet connection. Routing attacks and other network vulnerabilities can expose a user’s IP address. By correlating a user’s IP address with specific transaction times, it becomes possible to link their digital activity to a physical location and internet service provider, further eroding their pseudonymity.
- On-Chain Metadata and Smart Contracts: Beyond simple value transfers, the data stored on the blockchain can be much more revealing. Smart contracts can contain a wide range of metadata. A user interacting with a decentralized application (dApp) might unknowingly provide personal data, such as an email address or a username, that is then immutably recorded on the public ledger. Once this information is on the blockchain, it’s there for good, and anyone can see it.
- Combining On-Chain and Off-Chain Data: This is perhaps the most powerful method of de-anonymization. Attackers don’t just rely on the blockchain. They combine the public ledger data with information from traditional data breaches and social media. A large-scale data leak of passwords and login credentials can expose user information, which can then be cross-referenced with blockchain data. If a user’s email address is found in a leak and that same email is linked to a transaction on the blockchain (by signing up for a service), their on-chain activity is no longer private.
There’s actually a thrilling story in this regard. In August 2024, a teenager named Veer Chetal stole $243 million in Bitcoin, but his live-streamed heist was a complete failure. During the stream, he accidentally leaked his real name. This mistake was reinforced by his accomplices, who repeatedly called him “Veer” in subsequent recordings and chats. This error allowed crypto investigator ZachXBT to identify him and use blockchain tracing tools to track the stolen funds. Thankfully, Veer and his co-conspirators were arrested.
In conclusion, the idea that a public ledger is a leak-proof vault for personal data is a misconception. While your on-chain activity may not be useful to a not-so-average Joe like myself, through a combination of on-chain analysis, network vulnerabilities, and cross-referencing with off-chain data, your pseudonymity can be stripped away, revealing a detailed history of your activity.
 | PIVX: Your Rights. Your Privacy. Your Choice |