
How can you be sure that the data you send in Facebook,Whatsapp,Viber are secured? How are passwords of you accounts are stored in Database so no intruders have acess? There are many question related to data security these days as privacy and security are major concerns with increase in use of WWW.So, Today's topic is Encryption and Hashing.
What actually is Encryption?
In computing, encryption is the way by which text or a data is converted from a readable form to an encoded form that can only be decoded by recieving computer if they have access to a decryption key. Encryption is one of the most important methods for providing data security, especially for end-to-end protection of data transmitted across networks.Encryption is widely used on the internet to protect user information being sent between a client and a server, including passwords, payment information and other personal information that should be considered secured.
How does Encrytion works?
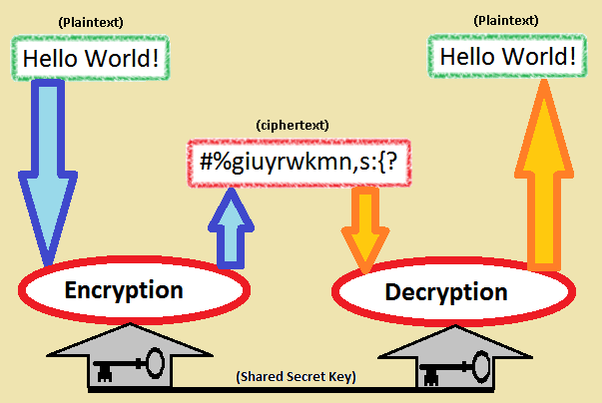
Normal Data called plaintext, is encrypted using an encryption algorithm and an encryption key. This process generates ciphertext that can only be viewed in its original form if decrypted with the correct key. Decryption is the inverse of encryption, following the same steps but reversing the order in which the keys are applied.The most common encrytion are :
Public Key Encryption
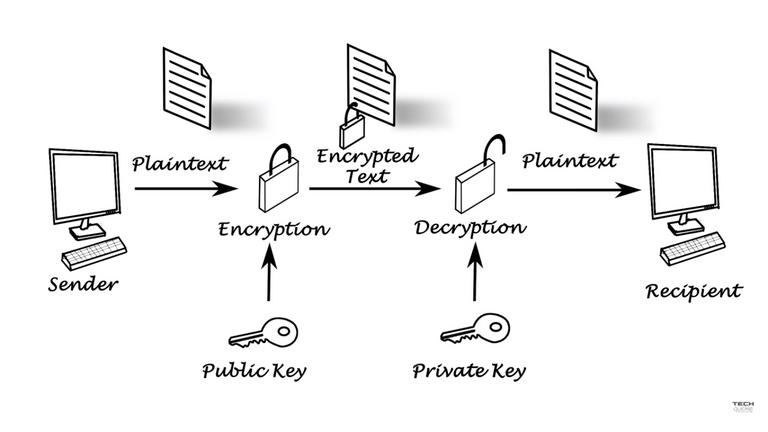
Public key Encryption, uses public and private keys to encrypt and decrypt data. The keys are simply large numbers that have been paired together but are not identical . One key in the pair can be shared with everyone; it is called the public key. The other key in the pair is kept secret; it is called the private key. When a computer wants to send the data to another computer,the recieving computer provides the public key of it to the sender. Once the public key is recieved,the sender encrypts the message using the public key recieved using a encryption algorithm. When the message is arrived to the reciver, the reciever decrypts the message using its own private key.So,it is not possible to decode the message unless the private key of the reciever is used. This way is mostly used in emails and secured signing in.
Hashing
So,you have learnt how the data are transferred in network.Then,How are password stored in databases so that if the database hacked then also the password is not revealed.Password are stored by using Hashing algorithms.When a user enters the password it is passed in hashing function which generates value which is then combined with a random text called salt to produce a hashed value.Then the hashed values and the salt are stored in database.When the application receives a username and password from a user, it performs the hashing operation on the password and compares the resulting hashed value with the password hash stored in the database for the particular user. If the two hashes are an exact match, the user provided a valid username and password.The benefit of hashing is that the application never needs to store the clear text password. It stores only the hashed value.
Example of database using hashing
| Username | Salt | Hashed Value |
|---|---|---|
| steemit | ccjskkekske23 | dfdjjelwpflw2p302342frr |
| dfjjsdjjspere | weew324423ejwr3432ew |
I am quite sure you understood how encryption and hashing works.But all the algorithms are quite perfect like md5 hashing algorithms can be hacked easily by a google search for a hash value. Hackers are always been searching for loop holes in the algorithm.If you have any questions feel free to comment below.
Very straightforward a easy to understand explaination of encryption and hashing. Thanks